New Ransomware Attack Alert: BadRabbit

A new strain of ransomware called BadRabbit is spreading through Eastern Europe. Likely created by the same authors as the Petya/Not Petya ransomware outbreak in June, BadRabbit ransomware uses a website to drop a fake Flash update and then drops its payload.
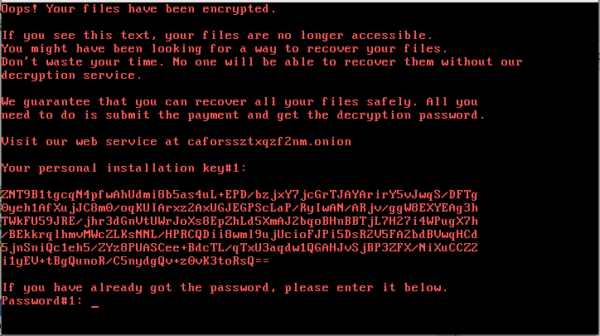
Bad Rabbit Lock Screen
Countries we know to be impacted so far are Russia, Ukraine, Turkey, Bulgaria, and Germany, with attacks centered on targets as wide-ranging as infrastructure, transportation, and media outlets. It is unknown at this time whether the attack will continue to spread, but it does have the same capacity for lateral infection (the ability to move deeper into a network and gain additional points of control) as the Petya/Not Petya ransomware.
Below is a view of the pay screen for Bad Rabbit, including its fascinating animated text. This is the most intricate pay screen we’ve ever seen, although it doesn’t seem to add any new functionality.
Cybercriminals are asking for 0.05 bitcoins, or $280, in return for the ransomed files. Customers of Grove Technologies Managed Malware are already protected from this threat. We detects it as Ransom.BadRabbit.
Concerned citizens who don’t have anti-ransomware technology should back up their most important files now (either to the cloud or to an external drive, which should be ejected after the backup is complete to avoid infection). Those who do have this type of security should be sure to run all updates and turn on real-time protection, if not already activated.
