The warranty dashboard Apple doesn’t provide… yet
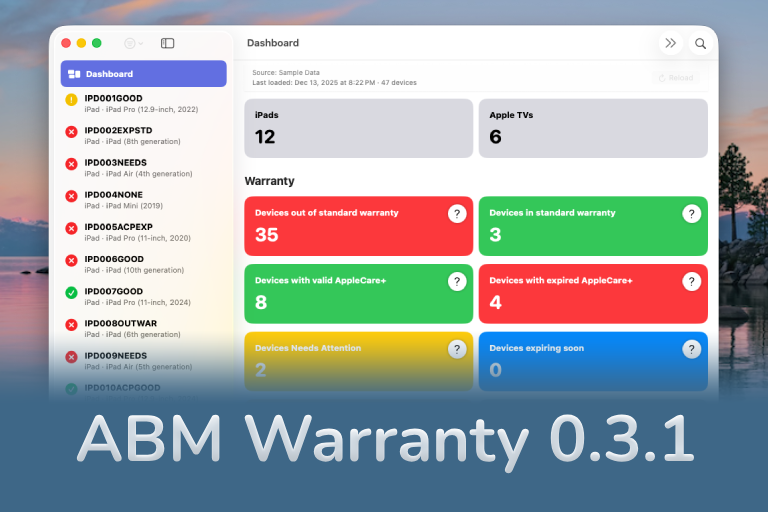
Download ABM Warranty Apple Business Manager and Apple School Manager are excellent systems of record. They tell you exactly what devices you own, who they’re assigned to, and how they’re enrolled. For inventory, they are authoritative. For risk, they are silent. What neither platform shows you is which devices are quietly becoming liabilities. Warranty expiration is not surfaced. AppleCare+ status is not prioritized. Devices that are weeks away from falling out of coverage look exactly the same as devices that are fully protected. Unless you manually click into individual records,...