Introducing ABM Warranty for macOS
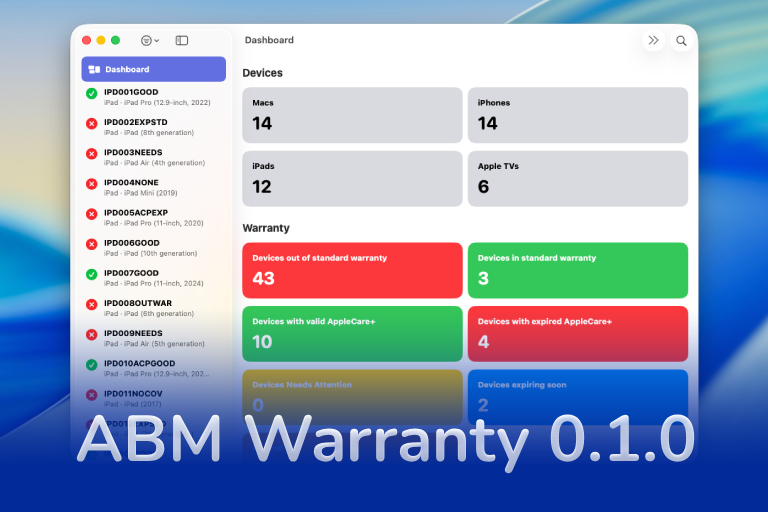
Blog Series Introducing ABM Warranty for macOS ABM Warranty 0.2.0 ABM Warranty 0.3.1 Introducing ABM Warranty for macOS A smarter, faster way to understand and manage warranty coverage across your organization. Download ABM Warranty 0.2.0 If you manage Apple devices at scale, you already know that Apple Business Manager (ABM) provides warranty data — but in practice, it’s extremely limited. It doesn’t provide workflow-friendly insights, it doesn’t surface actionable coverage states, and it doesn’t help you wrangle the ever-growing complexity of AppleCare+ renewals across hundreds or thousands of devices. That...